Updates to Threat Explorer and Email entity page
As part of Hunting improvements, we are making updates to the Email entity page, and Threat Explorer and Real-Time Detections. These updates should help provide additional data points and context for security analysts. These updates include:
Updates to Email entity Page will include:

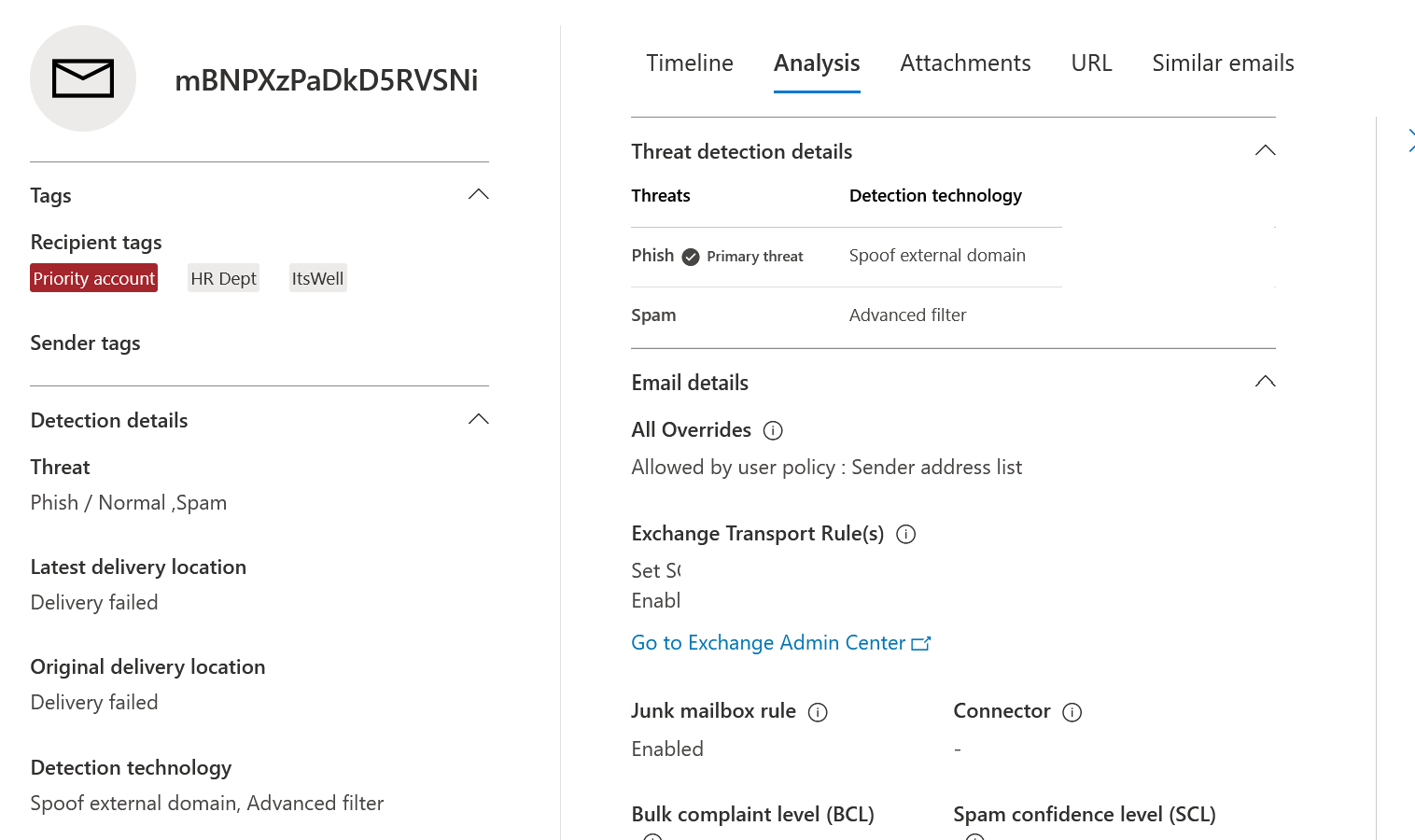
- A section around Threat Detection Details which will contain information around Threat, the corresponding detection technology and if the detection ran into any additional context.
- We will also light up additional email attributes like To, CC, Distribution list, Client information and forwarding (indicating if email forwarding was involved)
- Override information would include the Primary override and Source (Primary override is the override which impacted the delivery of the email) as well as any additional overrides that were applicable to the email.
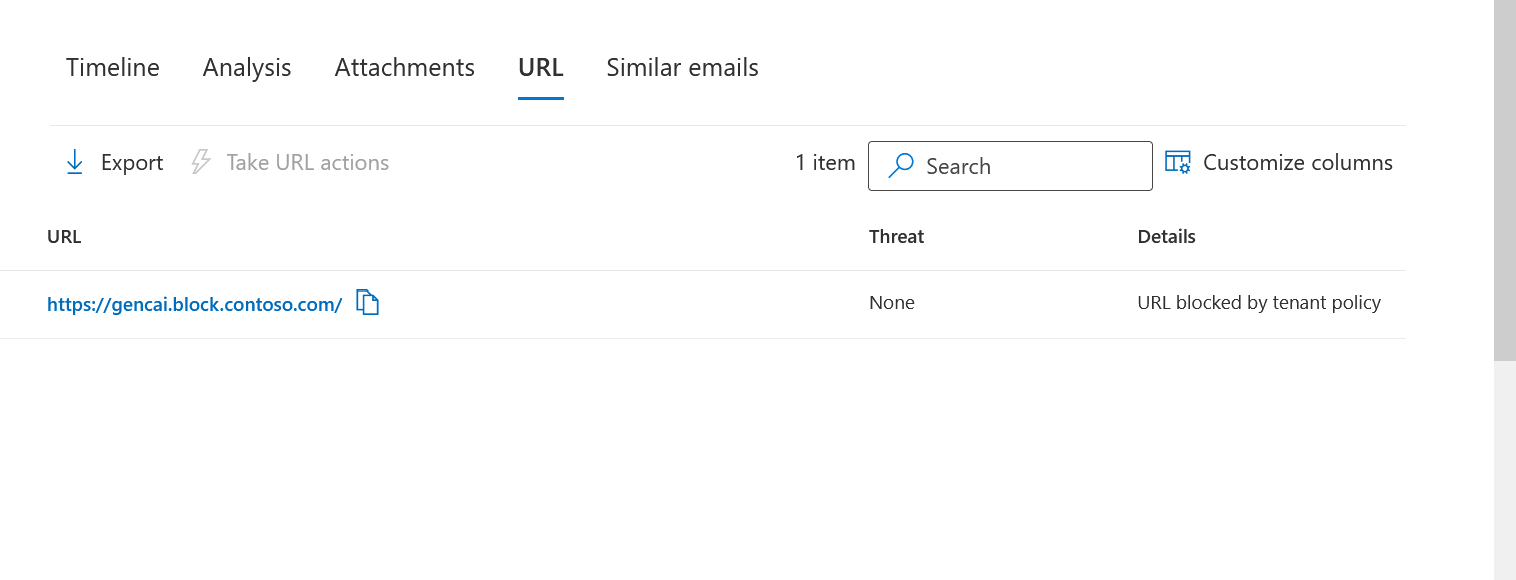
- If a URL or a File was allowed due to a tenant policy like Tenant Allow/Block list, then that information would be shown in the entity views as well.
Updates to Threat Explorer will include:
- Threat Explorer filters around System Override and System Override source would be renamed to Primary Override and Primary Override source to indicate the specific overrides which impacted the delivery of the email. This will help the analyst to locate malicious emails delivered due to potential config gaps, as well as identifying any tenant or user level configurations which have impacted the delivery of an email.
- In addition to the name updates for the above 2 filters, we will also be lighting up new filters to cover scenarios like if an email contained forwarding or not.
When this will happen:
We expect these updates to begin rolling out in early March and expect the rollout to be completed by late April.
How this will affect your organization:
Threat Detection Details and Overrides
As part of this change, we are updating the name System Overrides and System Overrode source filters to Primary override and Primary override source. Due to these new changes, you should re-evaluate your saved and tracked queries for these specific filters only.
Tenant URL Block in URL tab
What you need to do to prepare:
No specific action is required as you will start seeing the data and the new filters automatically once the roll out has been completed to your tenant. You should evaluate your Saved/Tracked queries if they contained any references to System Override and System Overrides Source.
Message ID: MC333945


 HANDS ON tek
HANDS ON tek
 M365 Admin
M365 Admin








No comments yet