Option to automatically allow Spoofing and Impersonation related message directly using Admin Submissions
Today security administrators can use the Submissions page in the Microsoft 365 Defender portal to submit email messages, URLs, and attachments to Microsoft for scanning
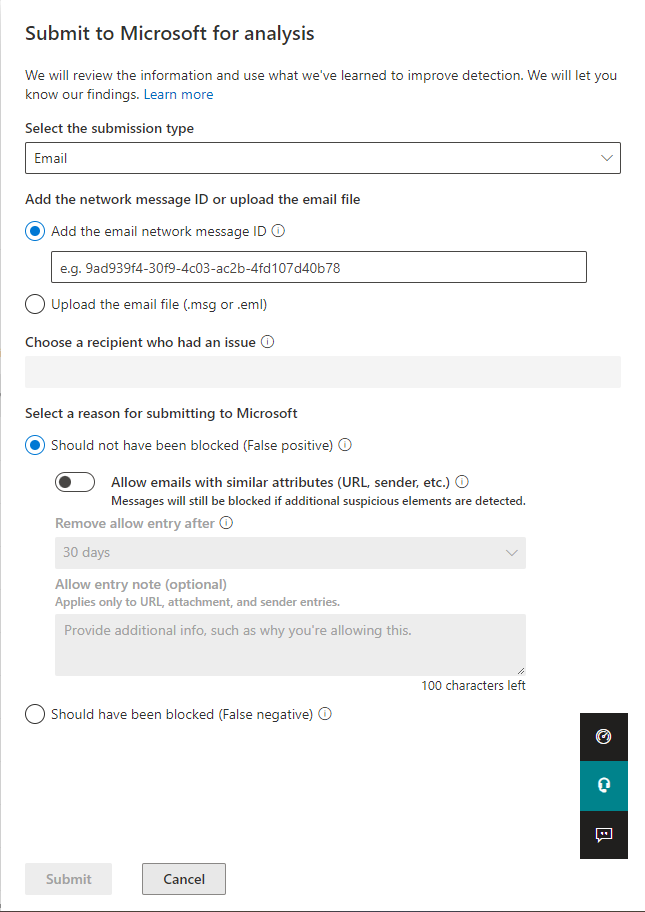
We are enhancing the email submission capability with an option to automatically allow Spoofing and Impersonation related emails from senders/infrastructure that were classified as legitimate by the admin, despite being initially blocked by the system. This will help mitigate false positives while the system continues to learn.

This message is associated with Microsoft 365 Roadmap ID 93366
When this will happen:
This feature has started rolling out and the rollout will complete by late June 2022
How this will affect your organization:
This enhances your ability to mitigate spoofing and impersonation related messages that you determine as False Positives.
You can tackle such False Positives easily while making admin submission by toggling “Allow emails with similar attributes.”
The allowed spoof sender domain pair entries will be created under Tenant allow block list – spoofing found at https://security.microsoft.com/tenantAllowBlockList.
The allowed impersonated domains or user entries will be created under the respective Anti Phishing Policy under https://security.microsoft.com/antiphishing.
What you need to do to prepare:
Note: Expiry date and notes won’t apply to spoof and impersonation allows created from this process.
You need to be informed of this change so that you can leverage this capability.
Message ID: MC394261


 HANDS ON tek
HANDS ON tek
 M365 Admin
M365 Admin








No comments yet